How To Recover Data After Exchange Server Zero Day Vulnerability?
| Confirmation has recently come in about a new Microsoft Exchange Server vulnerability, 2022, and that these two vulnerabilities affect the following MS Exchange servers: 2013, 2016, and 2019.
In their official report on the matter, Microsoft has identified the two vulnerabilities as CVE 2022 41040 and CVE 2022 41082. CVE 2022 41040 is an SSRF — a server-side request forgery and the second CVE 2022 41082 is an RCE vulnerability — RCE is short for remote code execution. |
|---|
Table of Content:
- What Are The Vulnerabilities?
- How Can The Risk Of Vulnerability Be Mitigated?
- How To Recover Your Server After An Attack?
- Wrapping Up
What Are The Vulnerabilities?
SSRFs make server-side applications send requests to an unauthorized/ unintended location, and can result in access controls for /admin being bypassed when the request is returned to the user.
The RCE CVE 2022 41082 Microsoft Exchange Server remote code execution vulnerability, (2022) allows for malicious code to be executed within server-side applications from the powershell of authorized users that possess admin privileges.
Microsoft is “working on an accelerated timeline to release a fix. Until then, we’re providing mitigation advice in order to help customers shield themselves from these attacks”, according to their statements.
This blog post by the Microsoft defense team contains a detailed analysis of how and where the vulnerabilities are exploited and how they work.
The CVE 2022 41040 vulnerability can only be deployed and exploited by users that are authorized, and they can then use CVE 2022 41040 to trigger the RCE (CVE 2022 41082) vulnerability, which they then use to launch their PowerShell code.
According to the Vietnamese outfit, GTSC ,that first discovered the vulnerabilities, the ongoing attacks that are exploiting these vulnerabilities may originate from a chinese-backed hacker group, because the powershell code that was deployed to exploit the Microsoft Exchange vulnerability, 2022 used a microsoft character encoding for simplified Chinese.
The vulnerabilities were reported on the zero day exchange website, which can be accessed here.
How Can The Risk Of Vulnerability Be Mitigated?
Firstly, and this goes without saying, admins need to block all exposed and unnecessary Powershell ports that have remote access authorized.
Secondly, there has also been released a series of guidelines concerning Exchange zero-day mitigation by way of URL rewrite instructions, which should be deployed as soon as possible, and followed to a T.
The advised mitigation to reduce exchange server vulnerability, for now is to add blocking scenarios (blocking rules) to the IIS (Internet Information Services) manager in the following path:
“Internet Information Services Manager >> Default Site >> Autodiscover >> URL Rewrite >> Actions” and then block the attack patterns that are known.
| S. No. | Vulnerability | Patch | Affected Servers |
|---|---|---|---|
| 1 | CVE 2022 41040 | Available, Use EOMT | 2013 - 2019 |
| 2 | CVE 2022 41082 | Unavailable, Block Ports | 2013 - 2019 including R2 |
That was the general form, but to apply the mitigation protocol to servers to stop the Microsoft Exchange Server vulnerability (2022), the following steps need to be followed:
- Launch The Internet Information Services Manager.
- Click on and expand the “Default Website”.
- Select “Autodiscover”.
- Navigate to the “Feature” view panel.
- Click on “Rewrite”.
- On the right side, you will see a panel labeled “actions”. Here, click on “add rules”.
- Select “Request Blocking”
- Add a string: “.*autodiscover\.json.*\@.*Powershell.”, barring the quotes.
- Expand this new rule you just created, and select “Edit Under Conditions”.
- Change the input conditional operator to REQUEST_URL from URL.
Under the Microsoft Exchange vulnerability (2022), infiltrators can also make use of the mentioned RCE (CVE 2022 41082), which is why Microsoft Defence Services also recommends blocking the following ports to make infiltration and exploitation harder:
- HTTP: 5985
- HTTPS: 5986
Users with administrator privileges can also run a command similar to selecting a string pattern:
“powershell.*autodiscover\.json”
Within their Internet Information Services Manager log files to check whether the Microsoft Exchange vulnerability (2022) has already affected their exchange servers.
Note: Microsoft has stated that only users who have pure on-premise deployments of exchange servers need to make these adjustments, but according to emerging reports, anyone with even hybrid deployments (a mix of on-premise and cloud deployment solutions) also needs to add the blocking rules — better to be safe than to be sorry.
However, users with only cloud-based deployments of their exchange servers need not take any action —
Microsoft will handle that for them on their own end.
How To Recover Your Server After An Attack?
1. Use The EOMT.
Microsoft has built a tool, called the EOMT (an abbreviation for Microsoft’s Exchange On Premises Mitigation Tool).
The tool can be installed from:
Given links, and, once the prerequisites have been met, Windows PowerShell needs to be run with administrator privileges enabled, and the script needs to be copied.
Then, all that needs to be done is to hit “enter”.
Users need to have an external internet connection that is sourced from their Exchange servers (with the IIS URL rewrite module as well as the MS Safety Scanner having been downloaded and loaded).
2. Install Patch Updates
Mitigation and remediation of your servers is of utmost importance right now, as an estimated 32,000 servers are still vulnerable, out of the global 400,000 in the latest figures about the Microsoft Exchange vulnerability (2022).
Visit this link to read Microsoft’s official blog post about who needs to take what action, whether your exchange server vulnerability has been patched or not.
Another thing you should do, if not completed already, is to install the Exchange Server Security Patch. If you face any issues, there is a troubleshooting manual for exchange server patch installations that can be found at the given link.
It is also advised to browse through the lists of known issues during patching, which can be found here and here, depending on your installation.
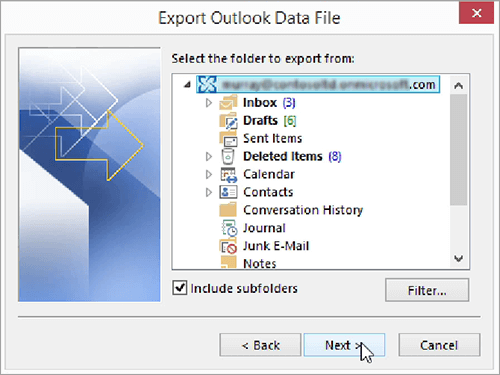
3. Backup Fresh Installation
You can use the:
Setup/m:recoverserver
To install a fresh copy of your server from your backups
Then proceed to delete or shut down the infected server(s).
4. Use Dedicated Software
This free to use exchange server recovery software allows administrators to recover data from downed servers, whether they are down due to an attack, a crash, a power failure, or any corruption otherwise.
It supports exchange servers 5.5 through 2019, including R2.
This allows you to recover mailboxes from affected servers and save them into a Personal Folders File (.PST).
Note: You need to run the EOMT script in an admin PowerShell before using the Stellar Exchange Recovery Software
Wrapping Up
The Microsoft Exchange Server vulnerability (2022) is a real threat, but nothing to be alarmed about — as you can see, there are plenty of mitigations and remediations that can be made to rectify and exchange server vulnerabilities that have opened up.
However, administrators of exchange servers are advised to:
Increase the frequency of their backup schedule
Backup to more than one local host, should the need for a new install and restore arise.
Most of the major vulnerabilities have been patched by Microsoft.
And new solutions are coming in every week or so, which means that the exploits will soon be closed, hopefully forever.